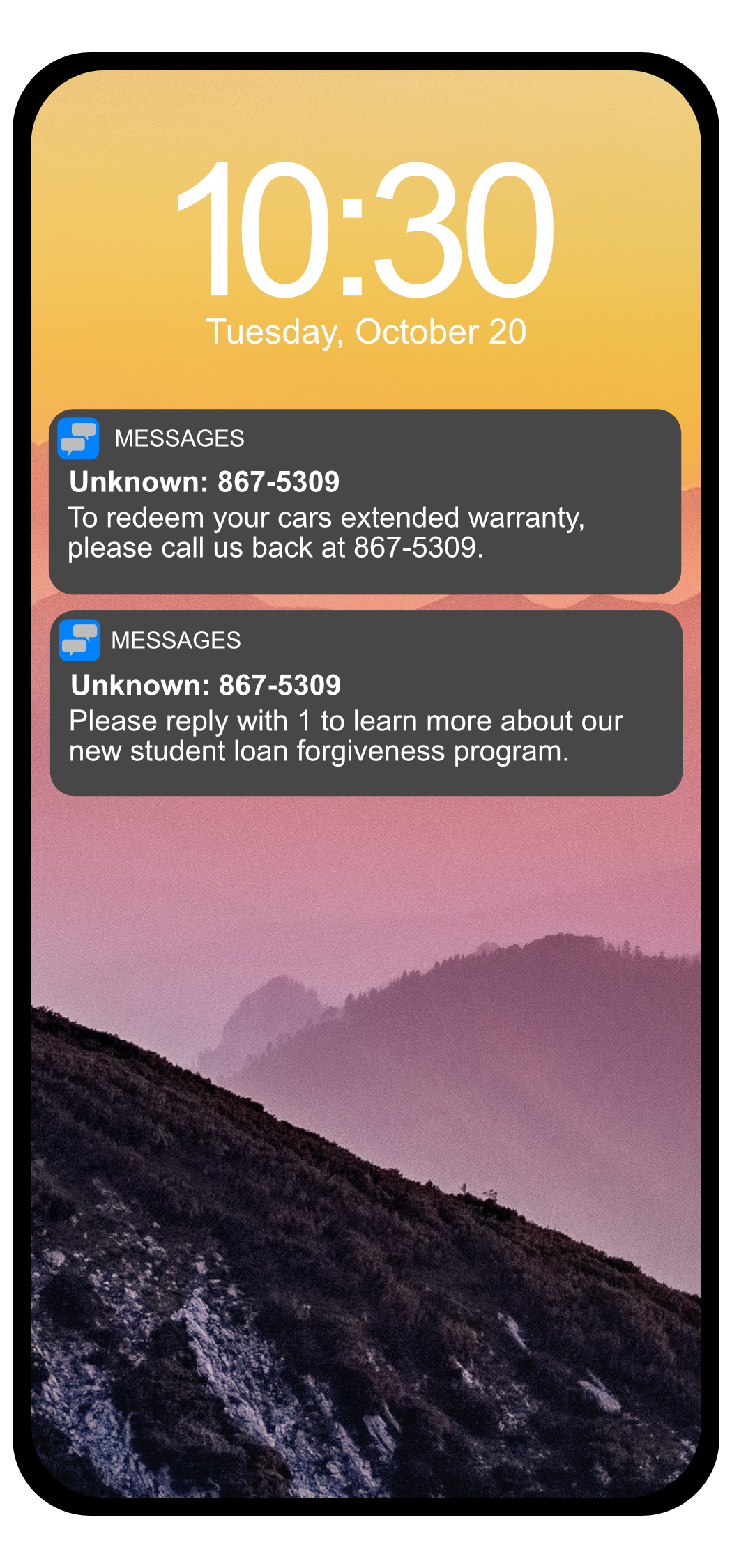
How to Avoid Being Scammed
When you see texts or emails like the ones pictured to the left, or get calls with similar content, the sender or caller is generally not legitimate. Due to an increased number of phishing phone calls and text messages, VSU Information Security would like to give you some tips to …